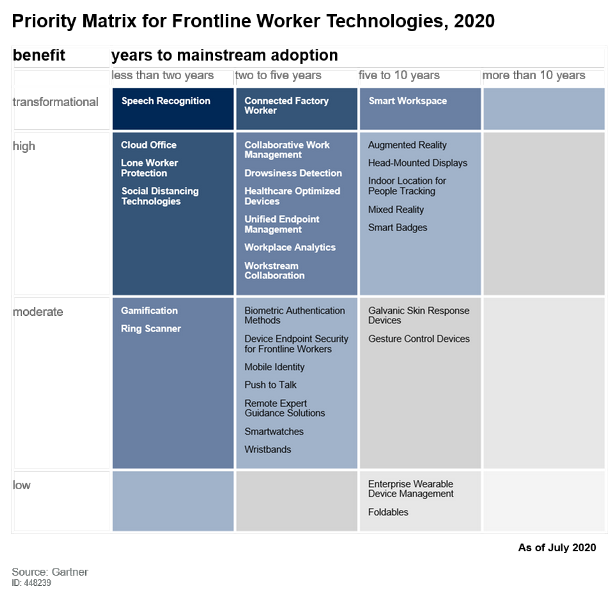
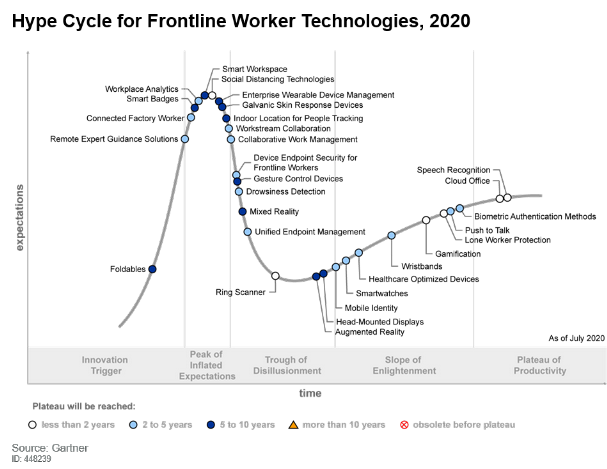
For six years ScaleFactor, an American startup, has been assuring small business clients that the program it developed can fully take over their finances and keep their books in order. As a result, the startup managed to obtain $ 100 million in investments but later investors discovered that all calculations were made manually by ordinary accountants, not by artificial intelligence. Forbes told its readers how this startup worked and how it collapsed.
Kurt Rathmann created ScaleFactor in 2014. The idea was to keep the clients’ books by means of special software and make accounting fully controlled and computerized with the help of artificial intelligence. In 2017 the company acquired support from the Techstars Austin business incubator with total investment of $ 2.5 million. Then a partner from Canaan Partners paid attention to the startup and Rathmann’s business got $ 10 million in investment.
Six months later, ScaleFactor received $ 30 million in a round led by Byron Deeter, a partner at Bessemer Venture Partners and an influential Silicon Valley cloud computing investor.
Despite the support from well-known investors, over time customers began to realize that something was going wrong. In April 2019, one of them requested termination of the contract when he saw that statements were not provided in real time, but once a month, as they were processed manually.
During the financial and legal examination, one of the potential investors discovered that the company had a special team of “client managers”, but later it turned out they were accountants.
ScaleFactor convinced clients that after the initial consultation, a program based on artificial intelligence would run their books. The software was not supposed to provide monthly statements, but to report data on its own portal in real time.
However, the program had a lot of bugs and errors, it could not be used for accurate sorting of operations, so the company hired a special team of accountants. They had to manually fill in customer statements and fix the program’s errors.
As a result, it turned out that ScaleFactor had only one tool with an automation component – an internal work environment engine, a managed list of tasks for employees, through which tasks were organized for maintaining the client’s accounting.
Yet the startup was viable and managed to attract investment in a new round of funding in early June 2019.The company’s employees were promised to double their bonuses if they could earn $ 800,000 on contracts with new clients. According to customers, managers began to offer discounts in exchange for a recommendation and signed contracts even without payment details. At the end of the month, the sales department was told that the targets were met, but a few weeks later it turned out that the bonuses were not worth counting on: some transactions were illegal, and the goals were not actually achieved.
ScaleFactor struggled to recruit new customers while existing clients demanded compensation. In October 2019 an employee who monitored customer churn reported a real risk of losing about $ 600,000 in annual revenue.
In January 2020, Kurt Rathmann announced that ScaleFactor intended to switch to a commercial platform model that would connect ordinary accountants with potential clients.
In much 2020 the United States was hit by Covid-19 pandemic and existing clients were no longer satisfied with the company’s activity. In the spring investors discussed the future of the startup but eventually decided to stop its functioning.
In June Rathmann announced about the planned closure of ScaleFactor. He complained that due to a drop in demand from small businesses amid the pandemic the company’s annual revenue, which was $ 7 million at the end of 2019, would almost halve.
ScaleFactor said it would lay off about 100 employees with a three-month severance package and return funds to investors.
Some former clients and employees believe that Covid was a “convenient excuse” and the startup’s management tried to hide the extent of the real damage.